Tutorial
The Solutions of iManager Security Vulnerabilities
The content below lists some common security vulnerabilities of iManager, and the solutions of these security vulnerabilities. If you meet the same security vulnerabilities, please follow the solutions:
-
CVE-2020-1967
Solution: Upgrade OpenSSL in iManager deployment machine to v1.1.1d. The download address: https://www.openssl.org/source/.
-
CVE-2018-15919
Solution: Upgrade OpenSSH in iManager deployment machine to v7.8 or higher.
-
Docker Remote API Unauthorized Access Vulnerability
Solution:
- Generate certificates, please refer to Docker Documentation.
-
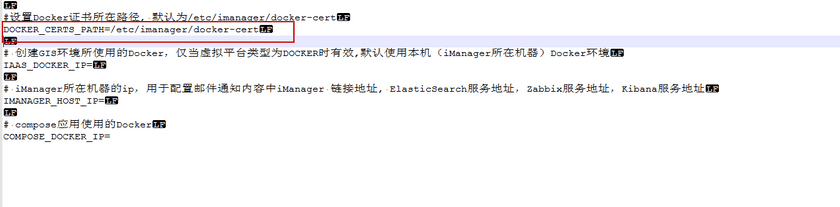
Open the environment variable configuration file. In the iManager installation directory(the directory that unzip from iManager installation package), enter to ‘supermap-imanager-docker’ directory, and open .env file:
vi .env - Configure the storage path of certificates. Fill in the certificate storage path in the variable ‘DOCKER_CERTS_PATH’, you can specify a path or keep in default, the default path is ‘/etc/imanager/docker-cert’.
- Create folders under the certificates storage path, the folders should be named by the machines’ IP of Docker environment which are providing the service for iManager.
- Store the certificates into the folders.
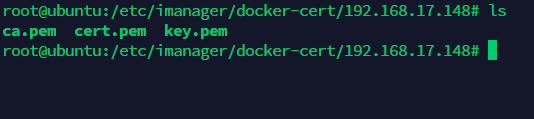
For example, the machine IP with Docker environment which is providing iManager services is 192.168.17.148. You need to create a folder named ‘192.168.17.148’ under the path ‘/etc/imanager/docker-cert’, and store the certificates ‘ca.pem, key.pem, cert.pem’ into the folder.
Notes:
If the services of iManager are providing by multiple machines with Docker environment, you need to create multiple folders according to the IP of machines, and store the certifictes to the Corresponding folders. -
Configure TLS Access for Docker
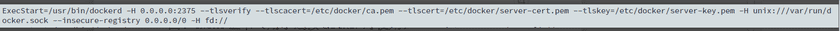
- Add the following parameters after the configuration in the file ‘docker.service’ or ‘docker.conf’:
--tlsverify --tlscacert=/etc/docker/ca.pem --tlscert=/etc/docker/server-cert.pem --tlskey=/etc/docker/server-key.pem- Update the configuration and restart docker service:
systemctl daemon-reload systemctl restart docker